This feature requires an Organization Admin role and is not available in local mode
Secrets are used to store security-sensitive credential information needed to access the data and catalog stores. Secrets are supported only in SaaS mode setup. The secrets page is accessible by navigating to Utilities -> Access Credentials, as shown below.
The Access Credentials page displays the list of registered credentials shown below.
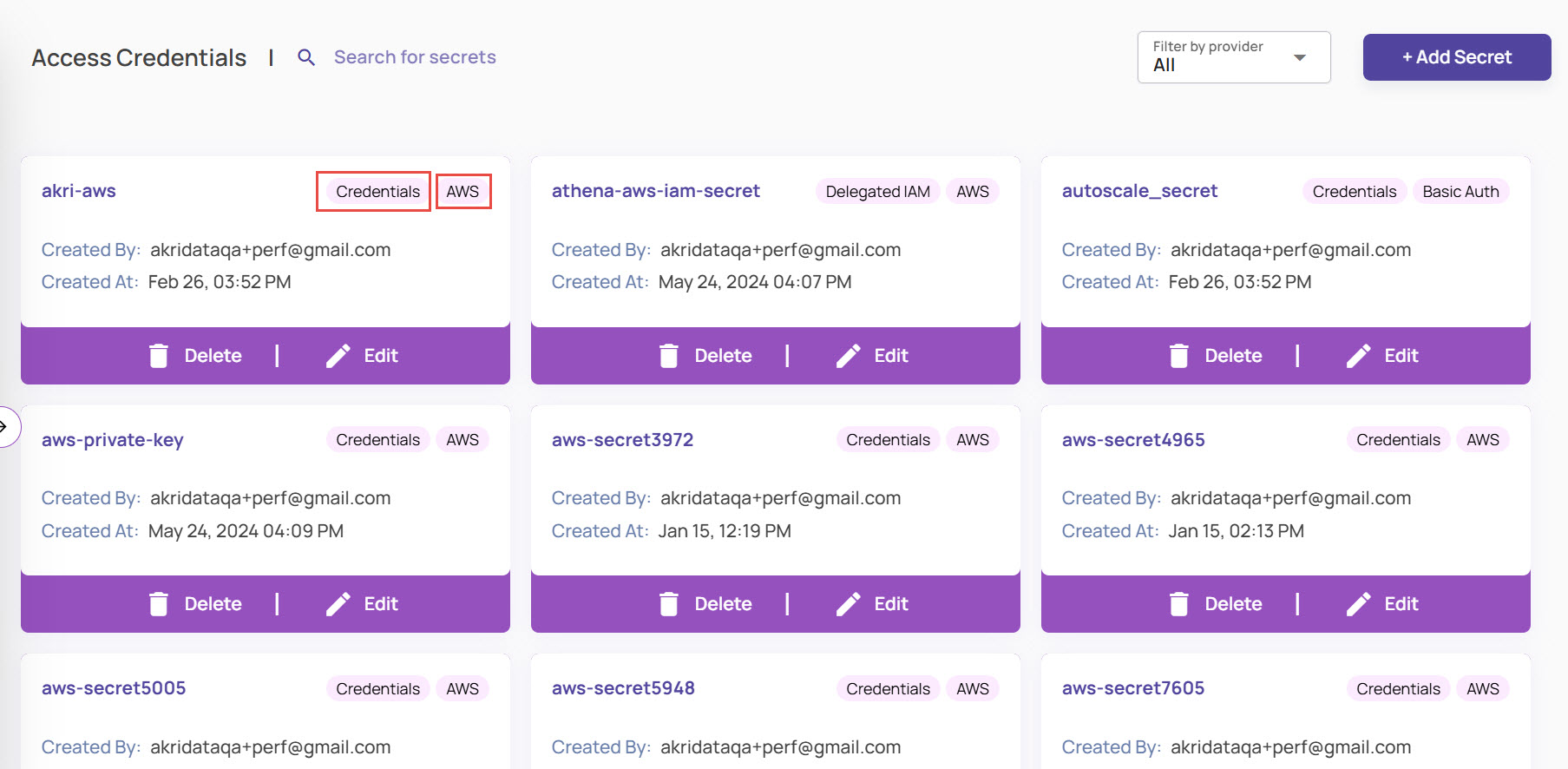 A secret can be of one of the following provider types.
A secret can be of one of the following provider types.
AWS: Supports two types, namely
Credentials: Captures an AWS access key and secret key credential information.
Delegated IAM: Captures the necessary information that allows access to AWS-hosted resources using a cross-account delegated IAM role, which is a more secure way of providing access. Please refer to this article for more details on delegated IAM roles.
Azure: Captures an Azure storage account key as a 'Credentials' type of secret.
GCP: Captures a Google service account key JSON file as a 'Credentials' type of secret - Reference
Basic Auth: Captures a username and password, typically used to store credentials to access a relational database as a 'Credentials' type of secret.
The page allows you to filter secrets by provider and search for a particular secret by name.
Adding Secret
Click the 'Add Secrets' button on the top right corner of the page.
A form as below opens up. Enter a name and select the 'Type' from the drop-down. Fill in the fields specific to the type and click 'Submit'.
.jpg)
Edit Secret
Click the 'Edit' button on the card corresponding to the secret to be edited. A form similar to 'Add Secret' opens up with credential fields allowed to be edited.
Delete Secret
Click the 'Delete' button on the card corresponding to the secret to be deleted and confirm the deletion.
Delete secret operation is irreversible.
The secret may be used by entities like containers, external catalogs, etc, and may result in operations on these entities failing. Please ensure the secret is not in use before deleting the secret.